CYBERSECURITY ENGINEERING
Within our cybersecurity offerings, our engineering solutions are pivotal, equipping organizations with robust defenses against evolving threats.
Access & Data Security
Through advanced technologies and expert strategies, we empower businesses to safeguard critical assets and sensitive data proactively.
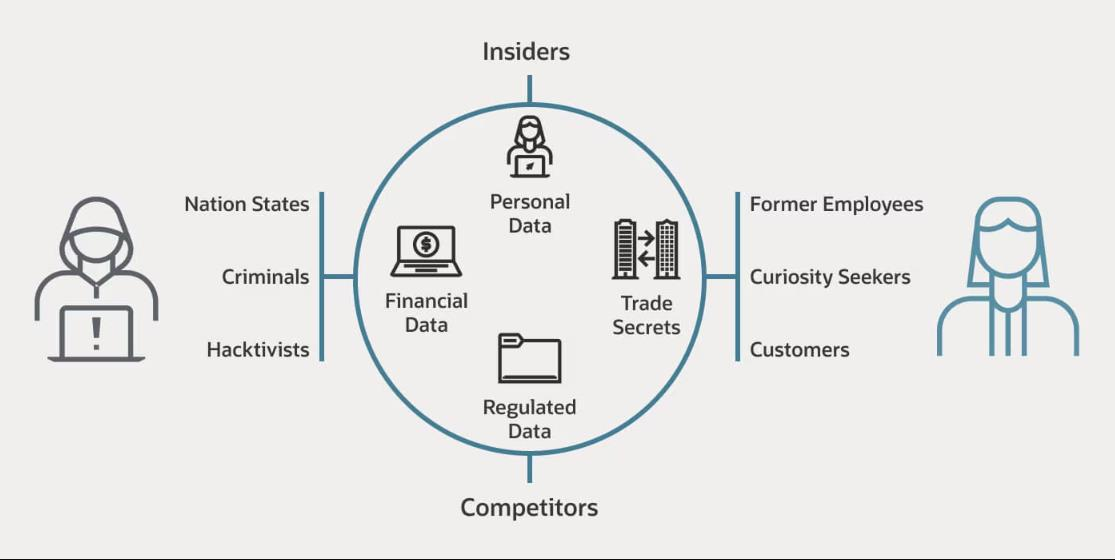
- Privileged and Access Management: Control and monitor privileged user access to critical systems and data to prevent unauthorized activity.
- Identity and Access Management: Manage and secure user identities and access privileges across the organization's network and applications.
- Endpoint Detection Response: Detect and respond to advanced threats and malicious activities on endpoints in real-time.
- Endpoint Protection Platform: Implement comprehensive security solutions to protect endpoints from malware, ransomware, and other cyber threats.
- Data Loss Prevention: Prevent unauthorized access, sharing, and leakage of sensitive data to maintain data confidentiality and compliance
- Data Activity Management: Monitor and analyze data access and usage to identify suspicious or anomalous behavior and prevent data breaches.
- Information Protection: Implement encryption and other security measures to protect sensitive information from unauthorized access or disclosure.
- Real-Time Transaction Monitoring: Monitor financial transactions in real-time to detect and prevent fraudulent activities and unauthorized transactions.
- Fraud Prevention & Account Takeover: Implement fraud detection and prevention measures to safeguard customer accounts and financial assets from fraudulent activities.
- Data Encryption: Encrypt sensitive data at rest, in transit, and in use to protect it from unauthorized access or interception.
- File Integrity Management: Monitor and ensure the integrity of critical system files and configurations to detect unauthorized changes or tampering.
- Multi-Factor Authentication: Enhance security by requiring multiple forms of authentication, such as passwords, biometrics, and one-time passcodes, to access systems and applications.
- Email Security: Protect email communications from phishing attacks, malware, and other email-borne threats to prevent data breaches and unauthorized access.
- Automated Penetration Testing: Conduct automated security assessments and penetration tests to identify and address vulnerabilities in systems and applications.
